WordPress Security is very important. It is much easier spending a few minutes securing WordPress, then spending hours recovering from being hacked. Security is becoming even more important because of the increase in automated brute force WordPress attacks. Below are a several tips to help secure WordPress and Apache. If you have your own server or VPS (like Linode or Vultr), to help reduce brute force attacks a very good solution is to use CloudFlare custom “Page Rules”. That will stop the requests before even getting to your server. WordPress security doesn’t sound like an exciting topic, but it is important so read on!
To help reduce other vulnerabilities follow the rest of the tips to improve WordPress security. The best advice for this is to stay updated and delete ALL unused themes and plugins. An old theme or plugin that is no longer being developed is potentially very easy for an attacker to exploit through an old vulnerability. This is most likely how an attacker puts a backdoor into a site since WordPress on its own is secure.
Any comments, questions or suggestions are welcome in the comments section at the bottom or from the contact page.
2013/12/31: Added information about minimizing number of plugins and OSSEC.
2014/09/29: CloudFlare offers free HTTPS.
2016/09/28: Update from 5G Blacklist to 6G Firewall, and add blocking for xmlrpc.php.
#1. Stay updated
Keep WordPress, themes and plugins updated. Also if you run WordPress on your own server or VPS keep apache, php5 and other packages up to date. This is the most important for WordPress security and also general web server security.
#2. Delete unused themes and plugins
Deactivating a theme or plugin that isn’t in use is not good enough. It needs to be completely deleted because the files can still be accessed (and exploited). This is probably the most common way an attacker will gain access to your server and a major benefit to improve WordPress security in general. Another good practice is to reduce the number of plugins running. If you don’t really need it, then delete it.
#3. Activate CloudFlare
Use CloudFlare’s free service to utilize them as a CDN and more importantly use their built in security features. You can also try to use IPtables to block brute force attacks, but a much simpler solution is to use CloudFlare.
The only negative about the free CloudFlare service is that it cannot use HTTPS. (That is a paid only feature).
To use CloudFlare you must be able to edit the DNS settings of your domain (to change the NS records).
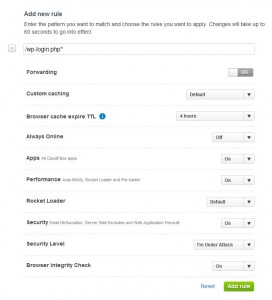
When using CloudFlare make sure to setup custom “Page Rules”. This will greatly reduce the login requests that make it to your server. What better way to improve WordPress security than to not even get the malicious requests!
Setup “Page Rules” using URL Pattern: “/wp-login.php*” (without quotes)
Change:
Always Online: Off
Security Level: I’m Under Attack
Browser Integrity Check: On
This will use Cloudflare to verify every login attempt (even your own) before getting to your server. After this change there will be very little traffic to the WordPress login page, since CloudFlare will be blocking most (if not all) of it.
#4. Remove the default “admin” account
Make sure the admin account is removed. This is one of the basic steps to improve WordPress security since automated attacks usually focus on this login, and if it isn’t there then it can’t be exploited.
Create another account with administrator privileges and then delete the admin account, or use a plugin that is mentioned below.
#5. Secure Passwords
Be sure to use a very secure password of random characters consisting of upper case, lower case, numbers and punctuation. Even if someone figures out the login name it will still be relatively secure if a strong password is used.
#6. Restrict access to WordPress login using .htaccess
It is a very good idea the restrict access to wp-login.php and the wp-admin directory to help with WordPress security and security in general. By restricting these pages based on an IP address it will cause anyone other than that IP to be blocked from logging in. CloudFlare is also a very good option (as previously mentioned) to help block access to logging in. If an attacker does get past the CloudFlare security, they will likely not get past this.
If you use CloudFlare use the first entry. Use either your exact IP or an IP range. You will probably need an IP range if your IP address changes often. Note that these requests still make it to your server. To further block access use CloudFlare page rules (as previously mentioned) if you can.
Be careful editing .htaccess files since you could potentially lock yourself out of WordPress. It’s best to have SSH access to your server.
For wp-login.php edit the main .htaccess file
If using CloudFlare (commented out line is for an IP range):
<files wp-login.php>
#SetEnvIf X-FORWARDED-FOR "^1\.*\.*\.*" allow
SetEnvIf X-FORWARDED-FOR "1.1.1.1" allow
order deny,allow
deny from all
allow from env=allow
</files>
If not using CloudFlare (commented out line is for an IP range):
<files wp-login.php>
order deny,allow
deny from all
#allow from 1.0.0.0/8
allow from 1.1.1.1
</files>
For wp-admin restriction edit the .htaccess file inside wp-admin directory
If using CloudFlare (commented out line is for an IP range):
SetEnvIf X-FORWARDED-FOR "1.1.1.1" allow
#SetEnvIf X-FORWARDED-FOR "^1\.*\.*\.*" allow
order deny,allow
deny from all
allow from env=allow
<Files admin-ajax.php>
Order allow,deny
Allow from all
Satisfy any
</Files>
If not using CloudFlare (commented out line is for an IP range):
order deny,allow
deny from all
allow from 1.1.1.1
#allow from 1.0.0.0/8
<Files admin-ajax.php>
Order allow,deny
Allow from all
Satisfy any
</Files>
#7. Reduce malicious URL requests
Use the 6G Firewall 2016 to reduce malicious URL requests. The list should be put at the beginning of the main .htaccess file. This helps in WordPress security since it stops an attack before it gets to the WordPress layer.
#8. Rename WordPress tables prefix
When first installing WordPress make sure to change the table prefix from the default “wp_”. If WordPress is already installed a plugin (like Acunetix WP Security, more on that below) can be used to easily make the change to something random like “notforyou_”. This will help WordPress security since attackers are less likely perform SQL injection attacks.
#9. Use WordPress Security Keys
Use the WordPress Security keys to make your stored passwords more secure and also by changing them it forces anyone that’s already logged in to re-authenticate. Overwrite the keys in the wp-config.php file after generating them here.
#10. Other tweaks using .htaccess
Remove access to readme.html and access to other unnecessary WordPress related files. This will improve WordPress security since it will be harder to determine the WordPress version. This also blocks other WordPress specific files. Blocking the xmlrpc.php file is a really good idea to prevent brute force login attempts unless you use the JetPack plugin, or another 3rd party tool to edit your posts.
Put at the bottom of main .htaccess file (After 6G Firewall 2016 and WordPress entries).
<files readme.html>
Order allow,deny
Deny from all
</files>
<files license.txt>
Order allow,deny
Deny from all
</files>
<files install.php>
Order allow,deny
Deny from all
</files>
<files wp-config.php>
Order allow,deny
Deny from all
</files>
<files xmlrpc.php>
Order allow,deny
Deny from all
</files>
#11. Remove WordPress version information
If an attacker doesn’t know the version of WordPress it can be harder to exploit since they can’t target a known vulnerability of an older version. This will help to improve WordPress security but there are many ways a determined attacker can gather this information. This will help with the basic attacks.
Edit the child theme’s functions.php file to include:
function wpnohead_remove_version() {
return '';
}
add_filter('the_generator', 'wpnohead_remove_version');
#12. Disable file editing in WordPress
If an attacker gains access through WordPress they can’t do much damage if they are unable to edit files on the server which will improve WordPress security.
Edit wp-config.php to include:
define( 'DISALLOW_FILE_EDIT', true );
define( 'DISALLOW_FILE_MODS', true );
#13. HTTPS for logins
If possible use HTTPS for logins. When using the free CloudFlare service this is not possible since only paid users can use HTTPS. CloudFlare now offers free HTTPS for everyone, so this will work if you are using CloudFlare.
If you can use HTTPS put this in wp-config.php (see info):
define('FORCE_SSL_LOGIN', true);
#14. Take regular backups
This doesn’t help WordPress security directly, but in general it is a very good idea. Use the plugin WP-DBManager to schedule automatic backups that can be emailed to you. If an attacker does get in this will help in the recovery.
#15. Security Plugins
Here are some security plugins that can come in handy to help with WordPress security.
Better WP Security – Can move login pages, rename admin account and change database table prefix. Moving login pages can help, since the attacker can’t easily find where to login (security through obscurity), but this isn’t needed if other measures are followed (Restrict access using .htaccess and CloudFlare page rules).
Acunetix WP Security – Can change database table prefix and perform some useful security audits. Checking files for date changes isn’t very useful since attackers can change timestamps of the files if they are already in your system.
Wordfence Security – Scans for known vulnerabilities. Another good feature is it scans core files, themes and plugins against WordPress.org repository versions to check their integrity. Verifying the security of your source. If/when you remove this plugin make sure to enable the option to remove all of the Wordfence options from your database, otherwise a large amount of data is sitting there. Option is at the bottom of the Wordfence ‘options’ page titled: “Delete Wordfence tables and data on deactivation?”
Limit Login Attempts – Useful if the same IP address keeps trying to login. But with the recent attacks there are many IP addresses trying to brute force the login and password. This plugin is no longer very useful.
AskApache Password Protect – Password protect logins using Apache built in security.
Google Authenticator – Two-factor authentication using the Google Authenticator app for Android/iPhone/Blackberry.
Threat Scan Plugin – Scans PHP files for backdoors added by hackers.
6Scan Security – Another option to use. Haven’t tried it yet.
All In One WP Security & Firewall – Another option to use. Haven’t tried it yet.
#16. Apache tweaks
If you have access to the main Apache configuration add the below lines. This isn’t specifically for WordPress security, it’s for the overall web server (Apache) security. Another obvious Apache security measure is to make sure Apache runs as a non-root user.
Prevent listing the index of folders.
In apache’s virtual host configuration files make sure to have:
Options -IndexesRemove server signature (from error pages, etc) and remove server version from header requests.
In httpd.conf add these lines to the bottom:
ServerSignature Off
ServerTokens Prod
#17. Use SFTP
Do not use regular FTP since it is insecure. FTP login and password information is sent unencrypted. This is a general security tip and not really specific to WordPress security.
#18. Monitor Apache logs
Check the Apache logs for any errors or abnormal URL requests. This seems trivial but it is a very important step to ensure your site is working smoothly and there is no abnormal behaviour.
If using CloudFlare, make sure to install the CloudFlare module for Apache so the visitor IPs are in the logs and not the CloudFlare IPs.
#19. Host-based Intrusion Detection System (OSSEC)
Install a program that runs on the server to monitor the system’s health and check for exploits. A program like OSSEC is a good choice.
Other Notes
Port knocking with IPTables for WordPress logins is another option to provide further security through obscurity, but this is complicated and beyond the scope of this post about improving WordPress security.
Fail2Ban is another option to scan the Apache logs but this causes excessive load on the server and is not needed with all the changes above.
Another unnecessary but interesting option is hiding a custom field in the login form and using a browser extension to set that field only in your browser. But again this is now not needed.
Any comments, questions or suggestions are welcome in the comments section below or from the contact page.
References
Hardening WordPress
WordPress Consultant
Prevent badware: WordPress
How to Protect WordPress Sites
6G Firewall 2016
How To Protect WordPress from Intrusion: Your Must-Read Checklist
How to Improve the Security of your WordPress Blog
The Definitive Guide to WP Security
How to Password Protect Your WordPress Admin (wp-admin) Directory
Protect your wp-admin with this quick .htaccess trick
Password Protect your WordPress Admin Folder

3 replies on “WordPress Security – How to Protect WordPress”
Some excellent tips. Going to try the CloudFlare page rule on wp-login. Could be really helpful in reducing the number of attempts to login.
Flippin awesome post EXACTLY what is need to be shared around the net cheers bud – you can check to see how well I’ve done later!
But me-thinks I’ll need a little help with this lol
Thanks for what reads like a careful exposition of issues and solutions. You have a typo under Other Notes: missing “is” in “but this complicated and beyond the scope of this post about improving WordPress security….”
Cheers, Fred