Ansible can use encrypted files, using a feature called Ansible Vault. This is great for sensitive information that you don’t want to store as a normal text file since you are able to encrypt this data in your source control.
If you are new to Ansible, read the getting started with Ansible post first.
Why use Ansible Vault?
You want to use Ansible Vault when you need to use sensitive data with Ansible, like a login and password, or SSH keys. Instead of storing this sensitive information in plain text, where anyone can read it when you save your Ansible Playbooks to your source control (like git), Vault uses an AES cypher to encrypt your data.
For more details, read the documentation.
Ansible Vault with Jenkins
Jenkins is software for Continuous Integration and Continuous Delivery. You can add plugins to Jenkins to extend its base features. And one handy plugin allows you to use Ansible with Jenkins.
Recently, the Ansible Plugin for Jenkins was updated to version 0.8.0, and as a result it now works seamlessly with Ansible Vault.
Install Ansible plugins for Jenkins
The first thing you need to install is the Ansible plugin for Jenkins.
Also, install the dependent plugin called Credentials Binding.
One thing to note is you can only read from encrypted Ansible Vault encrypted files. You cannot create or modify them using the Jenkins Ansible plugin. So you will still need to use the CLI to modify your encrypted files.
Add Vault password to Jenkins
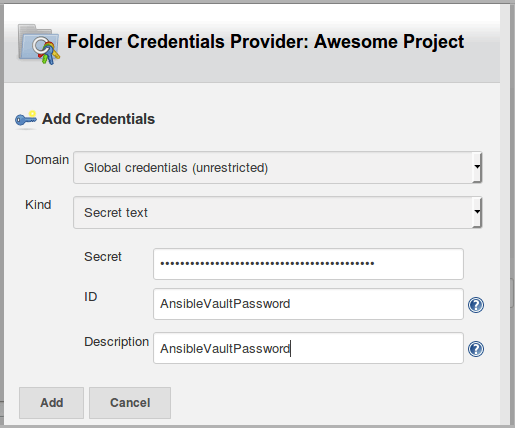
The simplest way to use Ansible Vault with Jenkins is to add your Vault password into a Jenkins Credential. Then you can bind the credential to an environment variable, or use it directly as a “Vault Credential”.
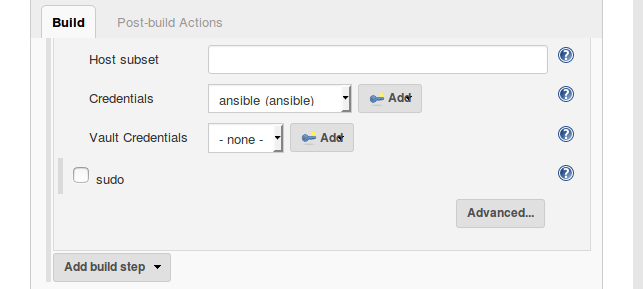
Configure your Jenkins freestyle project that uses an Ansible Playbook. If you have the newest version of the Ansible plugin, under the “Build” section you will now see an option for “Vault Credentials” since this is a new feature.
Add a new Jenkins Credential as “Secret text”, and enter your Ansible Vault encryption password.
Next, select the new Vault Credentials and you are ready to use your encrypted files in your Jenkins build job from your Ansible Playbooks.
Conclusion
In conclusion, you are now using Ansible Vault encrypted files automatically inside of your Jenkins build jobs. This helps you to keep your sensitive data secured in your source control. And Jenkins is helping you to deploy your Ansible Playbooks, while seamlessly decrypting your files.
Next, you can add a job to Jenkins that requires Ansible Vault. If you want to use Ansible for user management on Linux servers, check out the guide for User Management with Ansible.