When testing Docker and iptables I stumbled upon something interesting. It appears Docker uses the iptables INPUT chain in an undocumented way. Well that’s interesting.. Why Docker, Why?
I could find pretty much nothing about this, anywhere.
Wait, let’s take a step back. What am I talking about?
I was testing iptables with Docker. What a nightmare. Anyways, I noticed something strange with my three node Docker Swarm test VMs. Some very strange rules at the top of the iptables INPUT chain.
# iptables -nvL INPUT
Chain INPUT (policy ACCEPT 33477 packets, 8115K bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 policy match dir in pol ipsec udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100600"
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100600"
21 3669 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 policy match dir in pol ipsec udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100100"
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100100"
1 101 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 policy match dir in pol ipsec udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100200"
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:4789 u32 "0x0>>0x16&0x3c@0xc&0xffffff00=0x100200"What is that? Some kind of rules using a Docker port, and something about IPSEC.
Searching the internet has no information about this, that I could find at least. Only some random Docker issues on GitHub. It does have some similar details in the INPUT chain though.
Also found were two references to the Docker documentation.
The Docker documentation does have a pretty good section about iptables. But no mention of the INPUT chain. They very specifically say they only modify the DOCKER-USER and DOCKER chains in iptables.
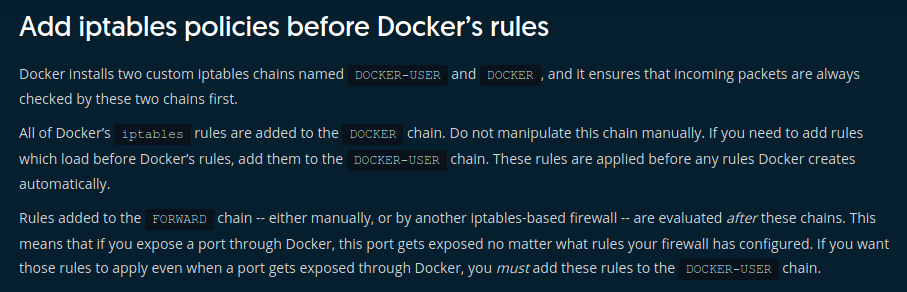
There’s also some information about the overlay network in the Docker documentation, but unfortunately it’s also very high level. No details about the Docker magic that makes all the networking work seamlessly! However, it does mention using IPSEC. Time to do some testing.
When testing in Docker Swarm, by starting containers which use an encrypted overlay I get those iptables rules in the INPUT chain. Fun!
Conclusion
Not a very exciting mystery. But very unexpected that Docker is modifying the INPUT chain in iptables! That changes a few thing when trying to secure Docker.. Hopefully other people weren’t relying on having the last rule in the INPUT chain.
Only Docker knows how their next version of Docker will behave. Anything a user does to try and secure Docker at the network layer is futile.
That being said, I’ve attempted to secure Docker with an iptables firewall. Check it out!